European end-to-end integrator for cyber security
In our today’s fast-paced and often unpredictable world, cyber threats against nations and societies increase continuously, are borderless and become progressively blurred and hybrid. Fighting against cyber threats means to always stay one step ahead of the cyber attackers. Building on our 30+ year heritage as integrated business of Airbus Defence and Space and our experience of protecting Airbus’ systems and platforms, we deliver tailored solutions to our customers and partners in the defence and aerospace domains.
What can we do for you
When cyber security is vital to the success of the mission, the Cyber business of Airbus Defence and Space delivers a portfolio of sophisticated products and solutions that answer the needs of our demanding customers.
Our inherent aerospace and defence domain knowledge, coupled with the expertise of our 450+ cyber experts, give us a unique understanding of the challenges our clients face every day. Combining state-of-the-art technologies and our strong European footprint in France, Germany, UK and Spain we ensure the protection of platforms and systems that in today’s increasingly digitalised and interconnected environment become more and more susceptible to cyber-attacks.
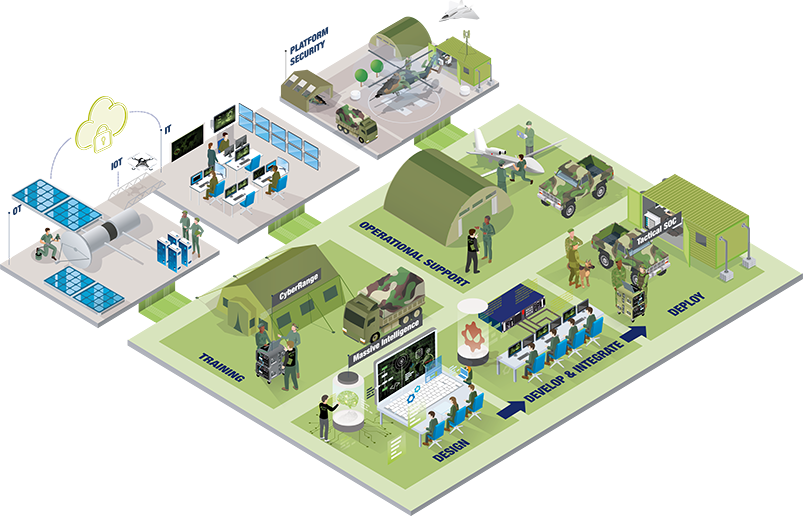
We work closely with armed forces, government agencies and institutional clients to design, develop, integrate and deploy tailored cyber security solutions as well as provide operational support all along the system lifecycle.

Our Portfolio
As the aerospace and defence industries continue to grow in scale, and as the digitalisation and interconnectivity increases, platforms and systems become increasingly susceptible to cyber-attacks. With security breaches increasing continuously in volume and sophistication, considerable resources are devoted today to keep these systems safe.
Our portfolio encompasses broad expertise in cyber project management, including:
- Crypto and Key Management systems
- Security Gateways
- Network and Endpoint Protection
- Aerospace Multi Messaging Systems
- Detection and Response Chains
- Cyber Attack Simulation Platforms
Our featured products
Our portfolio encompasses broad expertise in cyber project management, including
Airbus Defence and Space is recruiting
Do you want to be a part of it? Airbus Defence and Space Cyber is looking for talented and committed people just like you to join our team!
The Cyber business of Airbus Defence and Space is a leading European cyber security specialist in the aerospace and defence domains. While our products and solutions focus on solving the challenges of our customers and boost cyber resilience in the most demanding environments – it is our people that really make the difference. Our 450+ highly qualified cyber professionals come from diverse backgrounds and work together to develop and deploy tailored cyber solutions that protect governmental, defence and institutional customers. They are all driven by one ambition – to contribute to reinforcing the security and stability of our societies and nations.






